@atulsharma Sir, Please Help… ![]() I dont know where I am doing wrong…
I dont know where I am doing wrong…
We are not able to establish IPsec session. Please find the attached log.
===========================
!
crypto isakmp policy 10
encr 3des
authentication pre-share
group 2
lifetime 28800
crypto isakmp key 6 Password address 172.16.16.65
crypto isakmp key 6 Password address 172.16.56.65
crypto isakmp keepalive 60 20
!
!
crypto ipsec transform-set tscb esp-des esp-md5-hmac
mode tunnel
no crypto ipsec nat-transparency udp-encapsulation
!
!
!
crypto map tscbmap 1 ipsec-isakmp
set peer 172.16.16.65
set transform-set tscb
match address cryptofordc
crypto map tscbmap 2 ipsec-isakmp
set peer 172.16.56.65
set transform-set tscb
match address cryptofordr
!
!
interface GigabitEthernet0/1
description Connected to Airtel_Modem
ip address 10.255.255.1 255.255.255.252
ip tcp adjust-mss 1300
duplex auto
speed auto
crypto map tscbmap
!
!
interface Vlan1
description Connected to Branch LAN
ip address 172.16.146.65 255.255.255.224
!
!
ip route 0.0.0.0 0.0.0.0 10.255.255.2
!
ip access-list extended cryptofordc
permit ip 172.16.146.64 0.0.0.31 172.16.0.0 0.0.15.255
ip access-list extended cryptofordr
permit ip 172.16.146.64 0.0.0.31 172.16.32.0 0.0.31.255
!
==============HP RTR==========================
ipsec transform-set tscb
esp encryption-algorithm des-cbc
esp authentication-algorithm md5
ipsec policy-template ipsectemp 1
transform-set tscb
local-address 172.16.16.65
ike-profile tscbikeprofile
sa duration time-based 28800
ipsec policy wan 20 isakmp template ipsectemp
ike dpd interval 20 retry 60 on-demand
ike keepalive interval 20
ike keepalive timeout 60
ike identity address 172.16.16.65
ike profile tscbikeprofile
keychain tscbkey
local-identity address 172.16.16.65
match remote identity address 0.0.0.0 0.0.0.0
proposal 10
ike proposal 10
encryption-algorithm 3des-cbc
dh group2
sa duration 28800
ike keychain tscbkey
pre-shared-key address 0.0.0.0 0.0.0.0 key cipher xxxxxxx
===========================================================
RTR#ping 172.16.42.100 source 172.16.146.65
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 172.16.42.100, timeout is 2 seconds:
Packet sent with a source address of 172.16.146.65
*Jul 10 12:08:32.471: IPSEC(sa_request): ,
(key eng. msg.) OUTBOUND local= 10.255.255.1:500, remote= 172.16.56.65:500,
local_proxy= 172.16.146.64/255.255.255.224/256/0,
remote_proxy= 172.16.32.0/255.255.224.0/256/0,
protocol= ESP, transform= esp-des esp-md5-hmac (Tunnel),
lifedur= 3600s and 4608000kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*Jul 10 12:08:32.471: ISAKMP:(0): SA request profile is (NULL)
*Jul 10 12:08:32.471: ISAKMP: Created a peer struct for 172.16.56.65, peer port 500
*Jul 10 12:08:32.471: ISAKMP: New peer created peer = 0x318B84C0 peer_handle = 0x80000009
*Jul 10 12:08:32.471: ISAKMP: Locking peer struct 0x318B84C0, refcount 1 for isakmp_initiator
*Jul 10 12:08:32.471: ISAKMP: local port 500, remote port 500
*Jul 10 12:08:32.471: ISAKMP: set new node 0 to QM_IDLE
*Jul 10 12:08:32.471: ISAKMP: Find a dup sa in the avl tree during calling isadb_insert sa = 30008D1C
*Jul 10 12:08:32.471: ISAKMP:(0):Can not start Aggressive mode, trying Ma.in mode.
*Jul 10 12:08:32.471: ISAKMP:(0):found peer pre-shared key matching 172.16.56.65
*Jul 10 12:08:32.471: ISAKMP:(0):Input = IKE_MESG_FROM_IPSEC, IKE_SA_REQ_MM
*Jul 10 12:08:32.471: ISAKMP:(0):Old State = IKE_READY New State = IKE_I_MM1
*Jul 10 12:08:32.471: ISAKMP:(0): beginning Main Mode exchange
*Jul 10 12:08:32.471: ISAKMP:(0): sending packet to 172.16.56.65 my_port 500 peer_port 500 (I) MM_NO_STATE
*Jul 10 12:08:32.471: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jul 10 12:08:32.599: ISAKMP (0): received packet from 172.16.56.65 dport 500 sport 500 Global (I) MM_NO_STATE
*Jul 10 12:08:32.599: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Jul 10 12:08:32.599: ISAKMP:(0):Old State = IKE_I_MM1 New State = IKE_I_MM2
*Jul 10 12:08:32.599: ISAKMP:(0): processing SA payload. message ID = 0
*Jul 10 12:08:32.599: ISAKMP:(0): processing vendor id payload
*Jul 10 12:08:32.599: ISAKMP:(0): vendor ID is Unity
*Jul 10 12:08:32.599: ISAKMP:(0): processing vendor id payload
*Jul 10 12:08:.32.599: ISAKMP:(0): vendor ID seems Unity/DPD but major 0 mismatch
*Jul 10 12:08:32.599: ISAKMP:(0): vendor ID is XAUTH
*Jul 10 12:08:32.599: ISAKMP:(0):found peer pre-shared key matching 172.16.56.65
*Jul 10 12:08:32.599: ISAKMP:(0): local preshared key found
*Jul 10 12:08:32.599: ISAKMP : Scanning profiles for xauth …
*Jul 10 12:08:32.599: ISAKMP:(0):Checking ISAKMP transform 1 against priority 10 policy
*Jul 10 12:08:32.599: ISAKMP: encryption 3DES-CBC
*Jul 10 12:08:32.599: ISAKMP: hash SHA
*Jul 10 12:08:32.599: ISAKMP: default group 2
*Jul 10 12:08:32.599: ISAKMP: auth pre-share
*Jul 10 12:08:32.599: ISAKMP: life type in seconds
*Jul 10 12:08:32.599: ISAKMP: life duration (basic) of 28800
*Jul 10 12:08:32.599: ISAKMP:(0):atts are acceptable. Next payload is 0
*Jul 10 12:08:32.599: ISAKMP:(0):Acceptable atts:actual life: 28800
*Jul 10 12:08:32.599: ISAKMP:(0):Acceptable atts:life: 0
*Jul 10 12:08:32.599: ISAKMP:(0):Basic life_in_seconds:28800
*Jul 10 12:08:.32.599: ISAKMP:(0):Returning Actual lifetime: 28800
*Jul 10 12:08:32.599: ISAKMP:(0)::Started lifetime timer: 28800.
*Jul 10 12:08:32.627: ISAKMP:(0): processing vendor id payload
*Jul 10 12:08:32.627: ISAKMP:(0): vendor ID is Unity
*Jul 10 12:08:32.627: ISAKMP:(0): processing vendor id payload
*Jul 10 12:08:32.627: ISAKMP:(0): vendor ID seems Unity/DPD but major 0 mismatch
*Jul 10 12:08:32.627: ISAKMP:(0): vendor ID is XAUTH
*Jul 10 12:08:32.627: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Jul 10 12:08:32.627: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM2
*Jul 10 12:08:32.627: ISAKMP:(0): sending packet to 172.16.56.65 my_port 500 peer_port 500 (I) MM_SA_SETUP
*Jul 10 12:08:32.627: ISAKMP:(0):Sending an IKE IPv4 Packet.
*Jul 10 12:08:32.627: ISAKMP:(0):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Jul 10 12:08:32.627: ISAKMP:(0):Old State = IKE_I_MM2 New State = IKE_I_MM3
*Jul 10 12:08:32.715: ISAKMP (0): received packet from 172.16.56.65 dport 500 sport .500 Global (I) MM_SA_SETUP
*Jul 10 12:08:32.715: ISAKMP:(0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Jul 10 12:08:32.715: ISAKMP:(0):Old State = IKE_I_MM3 New State = IKE_I_MM4
*Jul 10 12:08:32.715: ISAKMP:(0): processing KE payload. message ID = 0
*Jul 10 12:08:32.743: ISAKMP:(0): processing NONCE payload. message ID = 0
*Jul 10 12:08:32.747: ISAKMP:(0):found peer pre-shared key matching 172.16.56.65
*Jul 10 12:08:32.747: ISAKMP:(1009): processing vendor id payload
*Jul 10 12:08:32.747: ISAKMP:(1009): vendor ID is DPD
*Jul 10 12:08:32.747: ISAKMP:(1009):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Jul 10 12:08:32.747: ISAKMP:(1009):Old State = IKE_I_MM4 New State = IKE_I_MM4
*Jul 10 12:08:32.747: ISAKMP:(1009):Send initial contact
*Jul 10 12:08:32.747: ISAKMP:(1009):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Jul 10 12:08:32.747: ISAKMP (1009): ID payload
next-payload : 8
type : 1
address : 10.255.255.1
protocol : 17
port .
Success rate is 0 percent (0/5)
RTR# : 500
length : 12
*Jul 10 12:08:32.747: ISAKMP:(1009):Total payload length: 12
*Jul 10 12:08:32.747: ISAKMP:(1009): sending packet to 172.16.56.65 my_port 500 peer_port 500 (I) MM_KEY_EXCH
*Jul 10 12:08:32.747: ISAKMP:(1009):Sending an IKE IPv4 Packet.
*Jul 10 12:08:32.747: ISAKMP:(1009):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Jul 10 12:08:32.747: ISAKMP:(1009):Old State = IKE_I_MM4 New State = IKE_I_MM5
*Jul 10 12:08:32.823: ISAKMP (1009): received packet from 172.16.56.65 dport 500 sport 500 Global (I) MM_KEY_EXCH
*Jul 10 12:08:32.823: ISAKMP:(1009): processing ID payload. message ID = 0
*Jul 10 12:08:32.823: ISAKMP (1009): ID payload
next-payload : 8
type : 1
address : 172.16.56.65
protocol : 0
port : 0
length : 12
*Jul 10 12:08:32.823: ISAKMP:(0):: peer matches none of the profiles
*Jul 10 12:08:32.823: ISAKMP:(1009): processing HASH payload. message ID = 0
*Jul 10 12:08:32.823: ISAKMP:(1009):SA authentication status:
authenticated
*Jul 10 12:08:32.823: ISAKMP:(1009):SA has been authenticated with 172.16.56.65
*Jul 10 12:08:32.823: ISAKMP: Trying to insert a peer 10.255.255.1/172.16.56.65/500/, and inserted successfully 318B84C0.
*Jul 10 12:08:32.827: ISAKMP:(1009):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Jul 10 12:08:32.827: ISAKMP:(1009):Old State = IKE_I_MM5 New State = IKE_I_MM6
*Jul 10 12:08:32.827: ISAKMP:(1009):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Jul 10 12:08:32.827: ISAKMP:(1009):Old State = IKE_I_MM6 New State = IKE_I_MM6
*Jul 10 12:08:32.827: ISAKMP:(1009):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Jul 10 12:08:32.827: ISAKMP:(1009):Old State = IKE_I_MM6 New State = IKE_P1_COMPLETE
*Jul 10 12:08:32.827: ISAKMP:(1009):IKE_DPD is enabled, initializing timers
*Jul 10 12:08:32.827: ISAKMP:(1009):beginning Quick Mode exchange, M-ID of 3491454410
*Jul 10 12:08:32.827: ISAKMP:(1009):QM Initiator gets spi
*Jul 10 12:08:32.827: ISAKMP:(1009): sending packet to 172.16.56.65 my_port 500 peer_port 500 (I) QM_IDLE
*Jul 10 12:08:32.827: ISAKMP:(1009):Sending an IKE IPv4 Packet.
*Jul 10 12:08:32.827: ISAKMP:(1009):Node 3491454410, Input = IKE_MESG_INTERNAL, IKE_INIT_QM
*Jul 10 12:08:32.827: ISAKMP:(1009):Old State = IKE_QM_READY New State = IKE_QM_I_QM1
*Jul 10 12:08:32.827: ISAKMP:(1009):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
*Jul 10 12:08:32.827: ISAKMP:(1009):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Jul 10 12:08:32.915: ISAKMP (1009): received packet from 172.16.56.65 dport 500 sport 500 Global (I) QM_IDLE
*Jul 10 12:08:32.915: ISAKMP:(1009): processing HASH payload. message ID = 3491454410
*Jul 10 12:08:32.915: ISAKMP:(1009): processing SA payload. message ID = 3491454410
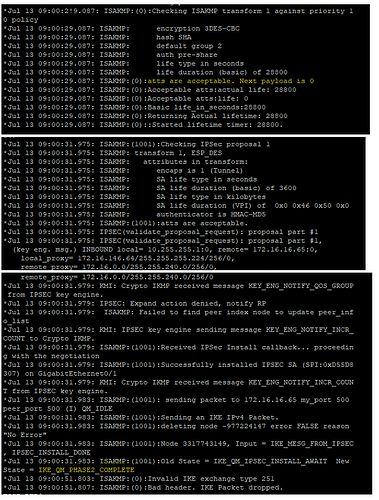
*Jul 10 12:08:32.915: ISAKMP:(1009):Checking IPSec proposal 1
*Jul 10 12:08:32.915: ISAKMP: transform 1, ESP_DES
*Jul 10 12:08:32.915: ISAKMP: attributes in transform:
*Jul 10 12:08:32.915: ISAKMP: encaps is 1 (Tunnel)
*Jul 10 12:08:32.915: ISAKMP: SA life type in seconds
*Jul 10 12:08:32.915: ISAKMP: SA life duration (basic) of 3600
*Jul 10 12:08:32.915: ISAKMP: SA life type in kilobytes
*Jul 10 12:08:32.915: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
*Jul 10 12:08:32.915: ISAKMP: authenticator is HMAC-MD5
*Jul 10 12:08:32.915: ISAKMP:(1009):atts are acceptable.
*Jul 10 12:08:32.915: IPSEC(validate_proposal_request): proposal part #1
*Jul 10 12:08:32.915: IPSEC(validate_proposal_request): proposal part #1,
(key eng. msg.) INBOUND local= 10.255.255.1:0, remote= 172.16.56.65:0,
local_proxy= 172.16.146.64/255.255.255.224/256/0,
remote_proxy= 172.16.32.0/255.255.224.0/256/0,
protocol= ESP, transform= esp-des esp-md5-hmac (Tunnel),
lifedur= 0s and 0kb,
spi= 0x0(0), conn_id= 0, keysize= 0, flags= 0x0
*Jul 10 12:08:32.915: Crypto mapdb : proxy_match
src addr : 172.16.146.64
dst addr : 172.16.32.0
protocol : 0
src port : 0
dst port : 0
*Jul 10 12:08:32.915: (ipsec_process_proposal)Map Accepted: tscbmap, 2
*Jul 10 12:08:32.915: ISAKMP:(1009): processing NONCE payload. message ID = 3491454410
*Jul 10 12:08:32.915: ISAKMP:(1009): processing ID payload. message ID = 3491454410
*Jul 10 12:08:32.915: ISAKMP:(1009): processing ID payload. message ID = 3491454410
*Jul 10 12:08:32.915: ISAKMP:(1009): processing NOTIFY RESPONDER_LIFETIME protocol 3
spi 806775851, message ID = 3491454410, sa = 0x30008D1C
*Jul 10 12:08:32.915: ISAKMP:(1009): processing responder lifetime
*Jul 10 12:08:32.915: ISAKMP (1009): responder lifetime of 1843200kb
*Jul 10 12:08:32.915: ISAKMP:(1009):Node 3491454410, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Jul 10 12:08:32.915: ISAKMP:(1009):Old State = IKE_QM_I_QM1 New State = IKE_QM_IPSEC_INSTALL_AWAIT
*Jul 10 12:08:32.915: IPSEC(key_engine): got a queue event with 1 KMI message(s)
*Jul 10 12:08:32.915: IPSEC(ipsec_get_crypto_session_id):
Invalid Payload Id
*Jul 10 12:08:32.915: Crypto mapdb : proxy_match
src addr : 172.16.146.64
dst addr : 172.16.32.0
protocol : 256
src port : 0
dst port : 0
*Jul 10 12:08:32.915: IPSEC(crypto_ipsec_create_ipsec_sas): Map found tscbmap, 2
*Jul 10 12:08:32.915: IPSEC(crypto_ipsec_sa_find_ident_head): reconnecting with the same proxies and peer 172.16.56.65
*Jul 10 12:08:32.915: IPSEC(create_sa): sa created,
(sa) sa_dest= 10.255.255.1, sa_proto= 50,
sa_spi= 0xE8F22ED3(3908185811),
sa_trans= esp-des esp-md5-hmac , sa_conn_id= 2017
sa_lifetime(k/sec)= (1843200/3600),
(identity) local= 10.255.255.1:0, remote= 172.16.56.65:0,
local_proxy= 172.16.146.64/255.255.255.224/256/0,
remote_proxy= 172.16.32.0/255.255.224.0/256/0
*Jul 10 12:08:32.915: IPSEC(create_sa): sa created,
(sa) sa_dest= 172.16.56.65, sa_proto= 50,
sa_spi= 0x30166C2B(806775851),
sa_trans= esp-des esp-md5-hmac , sa_conn_id= 2018
sa_lifetime(k/sec)= (1843200/3600),
(identity) local= 10.255.255.1:0, remote= 172.16.56.65:0,
local_proxy= 172.16.146.64/255.255.255.224/256/0,
remote_proxy= 172.16.32.0/255.255.224.0/256/0
*Jul 10 12:08:32.919: IPSEC: Expand action denied, notify RP
*Jul 10 12:08:32.919: ISAKMP: Failed to find peer index node to update peer_info_list
*Jul 10 12:08:32.919: ISAKMP:(1009):Received IPSec Install callback… proceeding with the negotiation
*Jul 10 12:08:32.919: ISAKMP:(1009):Successfully installed IPSEC SA (SPI:0xE8F22ED3) on GigabitEthernet0/1
*Jul 10 12:08:32.919: ISAKMP:(1009): sending packet to 172.16.56.65 my_port 500 peer_port 500 (I) QM_IDLE
*Jul 10 12:08:32.919: ISAKMP:(1009):Sending an IKE IPv4 Packet.
*Jul 10 12:08:32.919: ISAKMP:(1009):deleting node -803512886 error FALSE reason “No Error”
*Jul 10 12:08:32.919: ISAKMP:(1009):Node 3491454410, Input = IKE_MESG_FROM_IPSEC, IPSEC_INSTALL_DONE
*Jul 10 12:08:32.919: ISAKMP:(1009):Old State = IKE_QM_IPSEC_INSTALL_AWAIT New State = IKE_QM_PHASE2_COMPLETE
*Jul 10 12:08:34.471: Before encryption:
0DDAB4D0: 45000064 00790000 E…d.y…
0DDAB4E0: FF01A659 AC109241 AC102A64 0800B15B …&Y,…A,.*d…1[
0DDAB4F0: 00180001 00000000 00D1CC04 ABCDABCD …QL.+M+M
0DDAB500: ABCDABCD ABCDABCD +M+M+M+M …
*Jul 10 12:08:34.471: After encryption:
0DDAEB50: 45000098 01120000 E…
0DDAEB60: FF32CBCF 0AFFFF01 AC103841 30166C2B .2KO…,.8A0.l+
0DDAEB70: 00000001 9AFE1D53 876BC9F1 8F3BB9BB …~.S.kIq.;9;
0DDAEB80: F84B416D 8AB0C13D xKAm.0A= …
*Jul 10 12:08:34.471: post_crypto_ip_encrypt: Data just encrypted, 152 bytes
*Jul 10 12:08:34.471: Process switched encrypted packet
*Jul 10 12:08:34.587: crypto_sb_oce_alloc_fwd_handle: created forw_handle=3119E1DC using oce=0 type=0 for pak=3099AFC8, track=313EABE0
*Jul 10 12:08:34.591: Before decryption:
0E5DA410: 4500 0098DB2E 0000F632 E…[…v2
0E5DA420: FAB2AC10 38410AFF FF01E8F2 2ED30000 z2,.8A…hr.S…
0E5DA430: 000126D5 1BD6725F D24AAE97 4D6DD674 …&U.Vr_RJ…MmVt
0E5DA440: F48560A8 651F t.(e. ... *Jul 10 12:08:34.591: After decryption: 0E5DA430: 4500 00647EA8 E..d~( 0E5DA440: 00007E01 A92AAC10 2A64AC10 92410000 ..~.)*,.*d,..A.. 0E5DA450: B95B0018 00010000 000000D1 CC04ABCD 9[.........QL.+M 0E5DA460: ABCDABCD ABCDABCD ABCD +M+M+M+M+M ... *Jul 10 12:08:34.591: post_crypto_ip_decrypt: Data just decrypted, 100 bytes *Jul 10 12:08:34.591: PostDecrypt: pak cef switched *Jul 10 12:08:35.723: ISAKMP:(1008):purging SA., sa=300081D0, delme=300081D0 *Jul 10 12:08:36.471: Before encryption: 0DDAB350: 45000064 007A0000 E..d.z.. 0DDAB360: FF01A658 AC109241 AC102A64 0800A98A ..&X,..A,.*d..). 0DDAB370: 00180002 00000000 00D1D3D4 ABCDABCD .........QST+M+M 0DDAB380: ABCDABCD ABCDABCD +M+M+M+M ... *Jul 10 12:08:36.471: After encryption: 0DDAE0D0: 45000098 01140000 E....... 0DDAE0E0: FF32CBCD 0AFFFF01 AC103841 30166C2B .2KM....,.8A0.l+ 0DDAE0F0: 00000002 18E94CA9 2D804C6B B868D2DF .....iL)-.Lk8hR_ 0DDAE100: 952F6508 69841B71 ./e.i..q ... *Jul 10 12:08:36.471: post_crypto_ip_encrypt: Data just encrypted, 152 bytes *Jul 10 12:08:36.471: Process switched encrypted packet *Jul 10 12:08:36.587: crypto_sb_oce_alloc_fwd_handle: created forw_handle=3119E1DC using oce=0 type=0 for pak=3099AFC8, track=313EACB0 *Jul 10 12:08:36.587: Before decryption: 0E5D9610: 4500 0098DB2F 0000F632 E...[/..v2 0E5D9620: FAB1AC10 38410AFF FF01E8F2 2ED30000 z1,.8A....hr.S.. 0E5D9630: 0002E1C4 D6CF04BE 835F0CEB 9F1A1FB4 ..aDVO.>._.k...4 0E5D9640: 3DBB82B1 541C =;.1T. ... *Jul 10 12:08:36.587: After decryption: 0E5D9630: 4500 00647EA9 E..d~) 0E5D9640: 00007E01 A929AC10 2A64AC10 92410000 ..~.)),.*d,..A.. 0E5D9650: B18A0018 00020000 000000D1 D3D4ABCD 1..........QST+M 0E5D9660: ABCDABCD ABCDABCD ABCD +M+M+M+M+M ... *Jul 10 12:08:36.587: post_crypto_ip_decrypt: Data just decrypted, 100 bytes *Jul 10 12:08:36.587: PostDecrypt: pak cef switched *Jul 10 12:08:38.471: Before encryption: 0E95C3D0: 45000064 007B0000 E..d.{.. 0E95C3E0: FF01A657 AC109241 AC102A64 0800A1B9 ..&W,..A,.*d..!9 0E95C3F0: 00180003 00000000 00D1DBA4 ABCDABCD .........Q[$+M+M 0E95C400: ABCDABCD ABCDABCD +M+M+M+M ... *Jul 10 12:08:38.471: After encryption: 0DDAD9D0: 45000098 01160000 E....... 0DDAD9E0: FF32CBCB 0AFFFF01 AC103841 30166C2B .2KK....,.8A0.l+ 0DDAD9F0: 00000003 1E856698 1A3BDD20 C14B5524 ......f..;] AKU$ 0DDADA00: CA606D99 B8BA760E Jm.8:v. …
*Jul 10 12:08:38.471: post_crypto_ip_encrypt: Data just encrypted, 152 bytes
*Jul 10 12:08:38.471: Process switched encrypted packet
*Jul 10 12:08:38.583: crypto_sb_oce_alloc_fwd_handle: created forw_handle=3119E1DC using oce=0 type=0 for pak=3099AFC8, track=313EABE0
*Jul 10 12:08:38.583: Before decryption:
0E800390: 4500 0098DB30 0000F632 E…[0…v2
0E8003A0: FAB0AC10 38410AFF FF01E8F2 2ED30000 z0,.8A…hr.S…
0E8003B0: 00038DF7 50199DCD CB6DB075 4A1AA66B …wP…MKm0uJ.&k
0E8003C0: 7A87D68D 32C7 z.V.2G …
Jul 10 12:08:38.583: After decryption:
0E8003B0: 4500 00647EAA E…d~
0E8003C0: 00007E01 A928AC10 2A64AC10 92410000 …~.)(,.*d,…A…
0E8003D0: A9B90018 00030000 000000D1 DBA4ABCD )9…Q[$+M
0E8003E0: ABCDABCD ABCDABCD ABCD +M+M+M+M+M …
*Jul 10 12:08:38.583: post_crypto_ip_decrypt: Data just decrypted, 100 bytes
*Jul 10 12:08:38.583: PostDecrypt: pak cef switched
*Jul 10 12:08:40.471: Before encryption:
0DDABC50: 45000064 007C0000 E…d.|…
0DDABC60: FF01A656 AC109241 AC102A64 080099E8 …&V,…A,.*d…h
0DDABC70: 00180004 00000000 00D1E374 ABCDABCD …Qct+M+M
0DDABC80: ABCDABCD ABCDABCD +M+M+M+M …
*Jul 10 12:08:40.471: After encryption:
0DDAD650: 45000098 01180000 E…
0DDAD660: FF32CBC9 0AFFFF01 AC103841 30166C2B .2KI…,.8A0.l+
0DDAD670: 00000004 1DE39F5D 4BF2D048 5477E26D …c.]KrPHTwbm
0DDAD680: C631A08A EF41E867 F1 .oAhg …
*Jul 10 12:08:40.471: post_crypto_ip_encrypt: Data just encrypted, 152 bytes
*Jul 10 12:08:40.471: Process switched encrypted packet
*Jul 10 12:08:40.595: crypto_sb_oce_alloc_fwd_handle: created forw_handle=3119E1DC using oce=0 type=0 for pak=3099AFC8, track=313EACB0
*Jul 10 12:08:40.595: Before decryption:
0E9D0A90: 4500 0098DB31 0000F632 E…[1…v2
0E9D0AA0: FAAFAC10 38410AFF FF01E8F2 2ED30000 z/,.8A…hr.S…
0E9D0AB0: 00047753 A638ED45 70AD7791 FDC3CC59 …wS&8mEp-w.}CLY
0E9D0AC0: 8E2BF423 5A1B .+t#Z. …
*Jul 10 12:08:40.595: After decryption:
0E9D0AB0: 4500 00647EAC E…d~,
0E9D0AC0: 00007E01 A926AC10 2A64AC10 92410000 …~.)&,.*d,…A…
0E9D0AD0: A1E80018 00040000 000000D1 E374ABCD !h…Qct+M
0E9D0AE0: ABCDABCD ABCDABCD ABCD +M+M+M+M+M …
*Jul 10 12:08:40.595: post_crypto_ip_decrypt: Data just decrypted, 100 bytes
*Jul 10 12:08:40.595: PostDecrypt: pak cef switched
*Jul 10 12:08:54.047: ISAKMP:(0):Invalid IKE exchange type 251
*Jul 10 12:08:54.047: ISAKMP:(0):Bad header. IKE Packet dropped.
*Jul 10 12:09:14.535: ISAKMP:(0):Invalid IKE exchange type 251
*Jul 10 12:09:14.539: ISAKMP:(0):Bad header. IKE Packet dropped.
*Jul 10 12:09:22.919: ISAKMP:(1009):purging node -803512886
RTR#